Features Overview
Want a personalised Product tour? The ioGates Team would love to show you around!
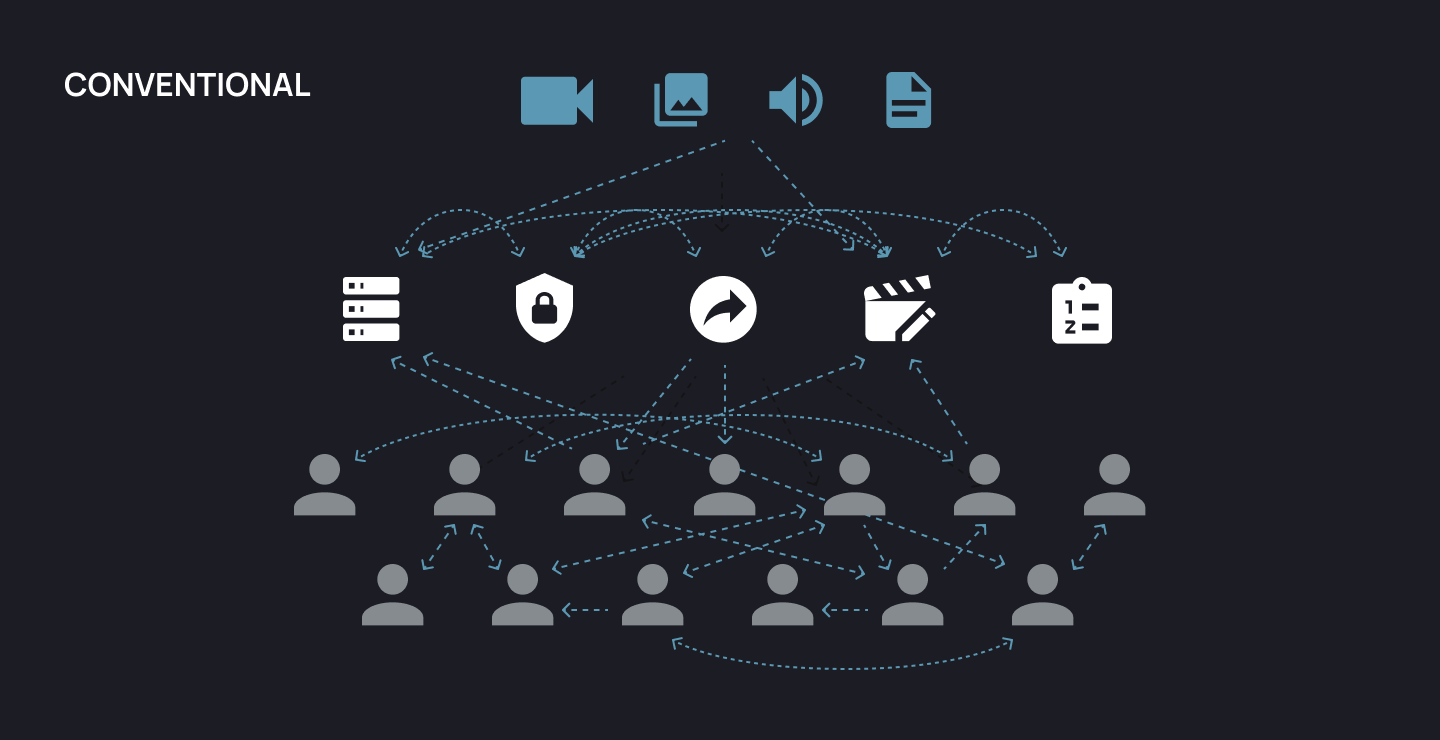
Share videos effectively with ShareLinks, blending control and customisation for stronger collaboration.
Secure every stage of your video production with robust security features for total peace of mind.
Transform videos smoothly with our intuitive tools, ensuring a seamless journey from raw footage to polished output.
Efficiently control your media with our streamlined library and versatile apps, enhancing your media experience.
01A Better Way

02Share Your Video
Simple Sharing with Maximum Control
ioGates ShareLinks give you optimal sharing control, efficient post-share management, fluid collaboration, and smart automation. These features integrate seamlessly into your post-production workflow, setting the stage for refined project execution and collaborative freedom.
02. A — ShareLinks
Seamless Sharing with ShareLinks

Control your content and adjust access, even after sharing.
Scale effortlessly without compromising function or experience.
Personalise your ShareLinks with custom branding options.
Bundle contacts into groups for faster sharing.
Manage share options such as master/proxy downloads, Comments, Transcriptions, Upload, Metadata, and Descriptions.
Get automatic notifications for new comments, new files, or both.
02. B — Post-Share Management
Modify contacts, groups, and permissions dynamically without resending.
Stay informed with automatic alerts for new content or comments.
Enhance security and accuracy with personalised watermarks and metadata.
Automatic email delivery confirmation.
Download .csv, text or PDF files of the contextual comments.
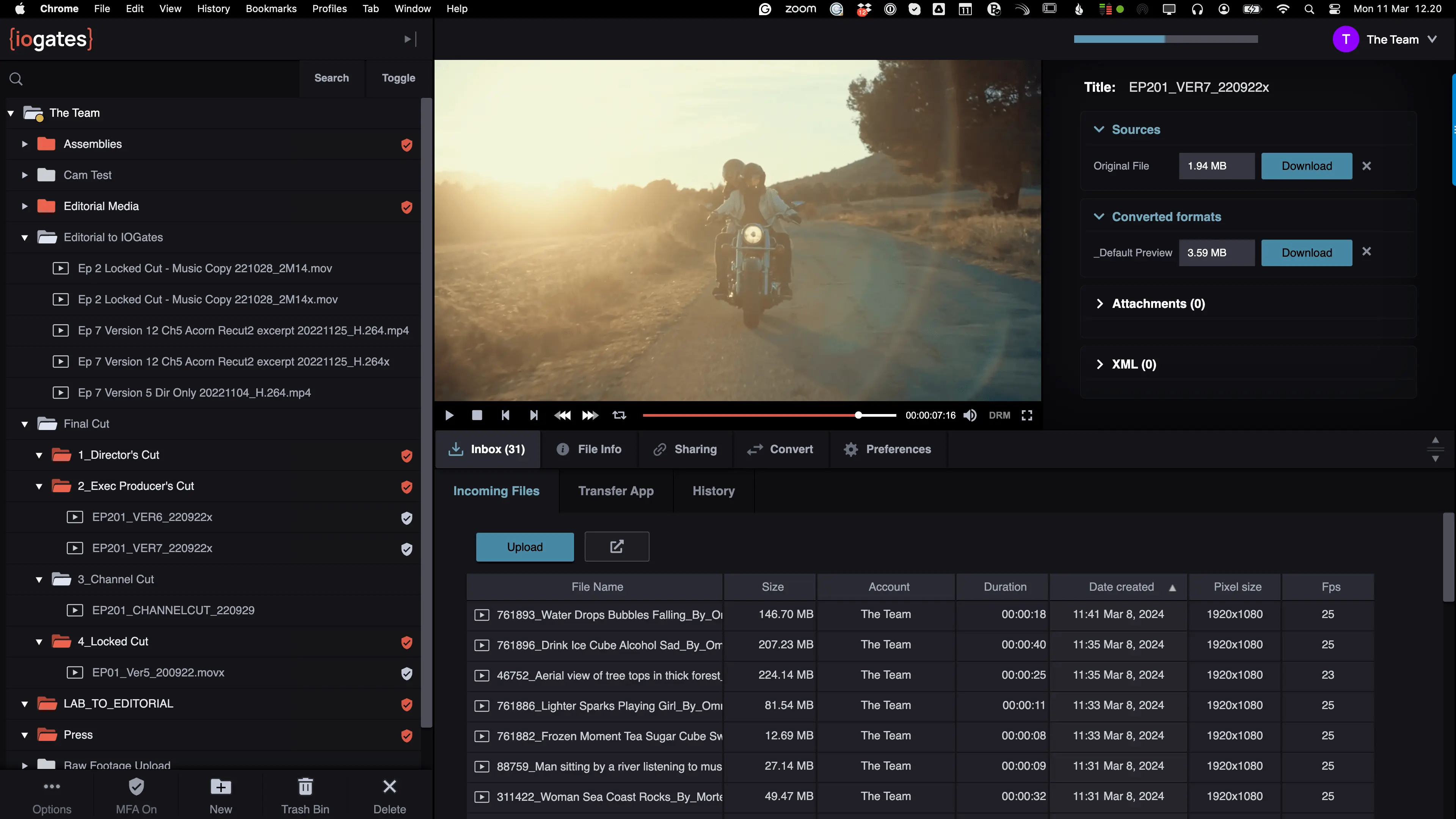
02. C — Collaboration
Centralise communication with contextual comments and frame-accurate timecodes.
Simplify bulk sharing and uploading by setting up group addresses.
Manage group sharing and permissions effortlessly.
Activate Two-Way Sharing so collaborators can upload footage to the same ShareLink.
Allow clients to view transcription on your ShareLinks
Enable users to download either master or any transcoded formats.
02. D — Automation
Combine ioGates features to create custom workflows.
Stay informed in real-time with automated notifications for new file additions and comments.
Leverage pre-defined triggers to automate tasks like transcoding and distribution.
Use QScan Automated Quality Control to ensure only files that pass your QC standards move forward.
03Secure Your Video
Unyielding Security for Every Production
In video production, security is paramount. iogates ensures a safe environment for sharing and managing your content at every stage, ensuring that all content is protected on the move and at rest.
03. A — Sharing Security
Share With Confidence at Every Stage

Control access so only authorised individuals can reach your shared content.
Opt for Digital Rights Management (DRM) protected video streaming.
Encryption ensures your content remains secure through its journey.
Protect your content from unauthorised access and distribution with highly secure links.
Utilise Two-Factor Authentication for an added layer of security on ShareLinks.
Set a ShareLink Password for simplified access, with a "one password for all users" functionality.
03. B — IT Security
Data Safeguards You Can Trust
Employs strong HTTPS SSL encryption, with non-essential ports and links blocked.
ioGates employees are trained in best practice security standards.
All power and networking have failover redundancies for continuous service.
Team iogates strictly comply with source code licensing, anonymised data, and assigning and distributing access keys.
Our data centres are ISO 27001 and SOC2 compliant and housed in a Tier 3 certified location.
We are TPN Trusted Partner Network certified.
Security Is Vital
For a Lars Von Trier Production
Customer Spotlight: Real-World Security Triumphs with iogates
“With all the hype around Lars Von Triers productions, the security aspect is crucial to us. Our previous system didn’t work, and we were in the midst of upping our security, So we changed to ioGates. It’s secure, easy to use, and Jesper and Tobias are always eager to help.”

04Transform Your Video
04. A — Sub-Clipping
Define in and out points with ease, ensuring precise segment selection.
Add metadata to clips for structured search and organisation.
Create multiple sub-clips from a source file, each with its own name.
Combine all sub-clips into one file
Select the output format for the sub-clip.

04. C — Subtitles
Overlay subtitling for real-time viewing Import and export subtitle files seamlessly for a smooth workflow.
Support for multiple languages
Burn-in subtitles on media files across any codec for permanent captioning.
04. D — Quality Control
Utilise QScan Automated Quality Control features within ioGates for detailed QC.
Run QC, get reports, and attach them to the source file for organised review.
Incorporate QC into automated workflows for streamlined quality assurance.
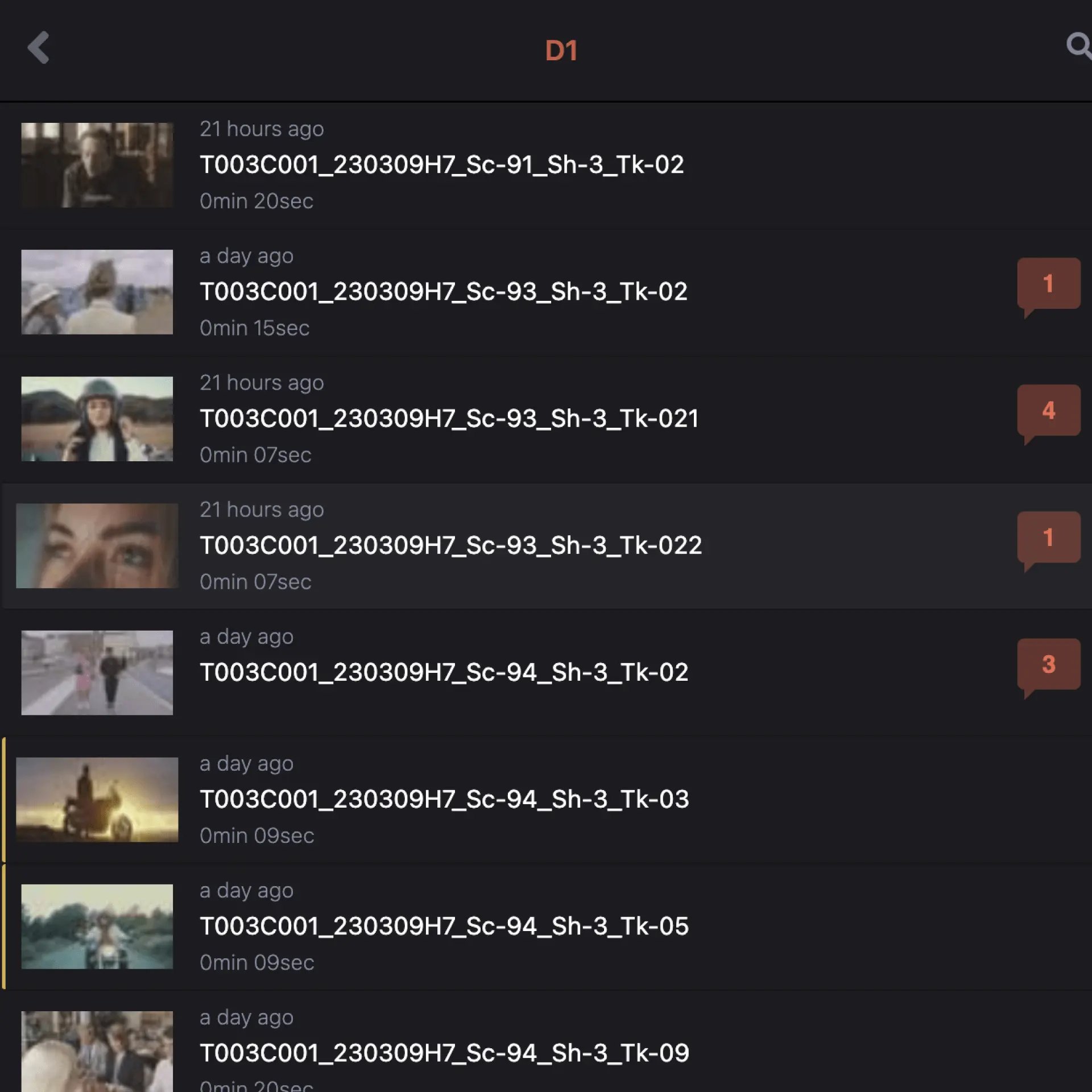
05Manage Your Video
05. B — Library
Navigate and manage media using our familiar, tree-based folders.
Move and copy files with drag and drop or keyboard shortcuts.
Link any folder with a local folder using the ioGates transfer app for auto upload and download.
Create Alias folders for advanced workflows.
Automate deletions on any folder, choosing either the master, proxy or transcoded files.
Archive individual files or folders while retaining proxy previews so you always can view your full library.
Restore single files from the archive.
.webp)
06. C — Playback
Enjoy a seamless playback experience across devices.
Multimedia ready with audio, image, PDF, and text file support.
Familiar J,K,L keyboard controls for easy navigation.
Built-in tools such as subtitles. chapter markers, frame stepping, looped playback, and more.
06. D — Apps
The Transfer app ensures automatic and reliable file transfers.
No need for passwords; Use ioGates share links to authenticate with the Transfer app.
Any folder can be linked with your clients or partners' local folders securely.
Upload your media on the go with your mobile.